Onboarding taking too long? PrivOps can help!
Why not Automate IAM?
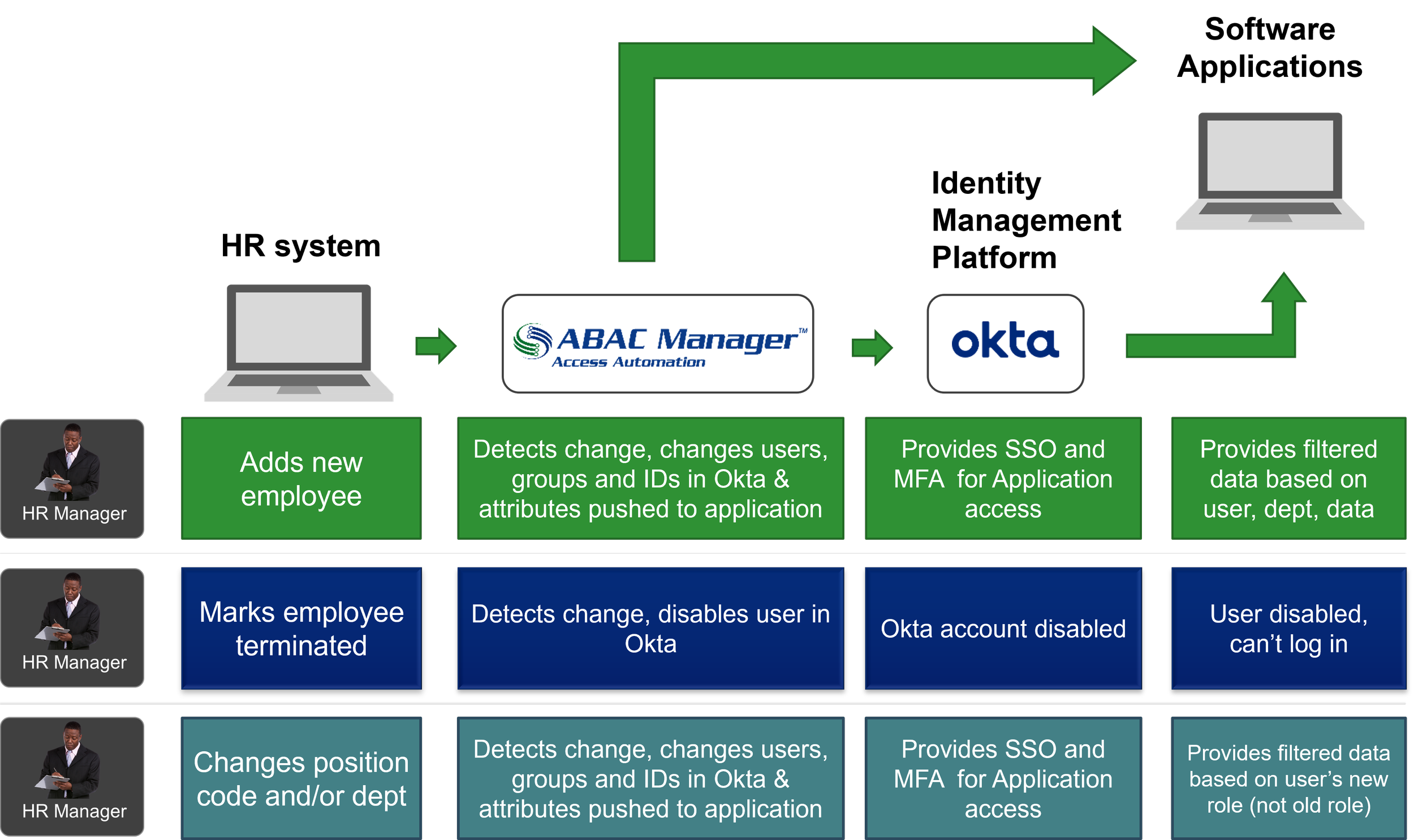
ABAC Manager provides the orchestration, data governance, data transformation, data validation, error notifications and integrations required for end-to-end automation of Identity, Governance and Administration (IGA).
Features
Every user always has the right level of access to data and systems
Benefits
Can easily share data both within and outside the organization knowing access to data and applications is always correct
Access permissions are automatically updated as users are onboarded, change roles or depart
Users immediately have access to the systems they need to do their jobs
No more zombie users or shadow superusers
Once configured, ABAC Manager is only used when the upstream systems of record change their data formats
No more emails or service tickets for user onboarding, offboarding and role or status changes
ABAC Manager creates a standard authoritative data standard for user data
Minimal to no integration work is required when migrating to different access management systems (Okta, Azure AD, etc.) or HR systems (Workday, ADP, Paycom, etc.)
The ABAC Manager no-code interface
ABAC Manager provides a simple and intuitive interface for non-technical operations personnel to manage data mappings, workflows, error notifications, and more.
ABAC Manager provides a powerful regular expression based interface that makes it easy to map multiple fields like EmployeeTitle, PositionCode or any other data fields into user roles and group mappings.
ABAC Manager provides data validation and error handling to insure the integrity of data extracted from HR and other systems of record for the purposes of automation.
ABAC Manager Overview
Attribute Based Access Control (ABAC) automates the processes for providing and revoking user access to IT systems and data. PrivOps’ ABAC Manager manages those automations.
Automation workflows aggregate, validate, and map information from HR and other systems of record to automate managing security groups, roles and mapping users to roles as necessary for Identity and Access Management (IAM).